Setting up your security scheme
You can control the extent to which your users have access to the system by setting up appropriate user groups and then restricting access to specific facilities to only certain groups. You give each group you intend to use a name that reflects some role, e.g. purchasing, sales, production, etc. You then assign these groups to your users and also to the facilities you want to allow them to use. Access is only allowed when both the user and the facility they want to use are members of the same group. Each user and each facility can be members of any number of groups.
The first thing you must do is decide what group names you want to use. They can reflect roles or departments or anything else that is meaningful to you. Then you allocate groups to users and finally you associate groups with functions within the system.
Access to the security system can be gained from most places by pressing the F9 key or the ![]() icon. Or you can select the Manage User Groups function from the Processes menu:
icon. Or you can select the Manage User Groups function from the Processes menu:
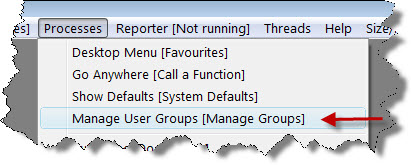
Depending on where you were, you will see either a form like this:
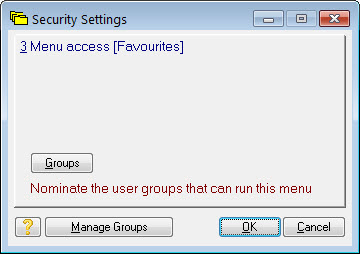
Press Manage Groups.
Or like this:
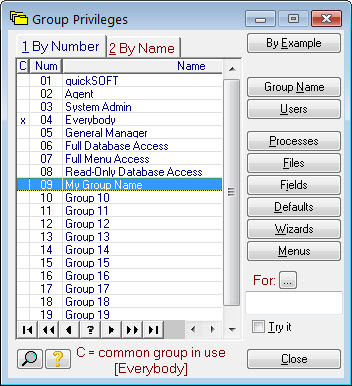
This shows the list of group names. On installation the first eight groups are preset. You would normally leave these alone. The remaining groups (9 to 30) can be named and set-up as you like.
The preset groups are used as follows:
quickSOFT |
This is reserved for use by Match-IT staff for system maintenance and diagnostic purposes. You cannot change this group. |
Agent |
The special Agent user uses this when it performs the overnight housekeeping and scheduling functions. You would normally leave this group as is. |
System Admin |
This group has access to all the system configuration functions. It's intended to be used by your IT staff to make configuration changes. |
Everybody |
This group provides access to the minimum functions required to log-in to the system. Everybody that needs to be able to log-in should be a member of this group. |
General Manager |
On installation this group has access to everything. You should reserve this group for use by people with very high authority and trust within your organisation. The Manager user is a member of this group. |
Full Database Access |
This group provides un-restricted access to all databases. This is useful if you want to setup a simple security scheme purely based on restricting access to processes (i.e. forms and browses). Assigning users to this group removes any consideration of database access. |
Full Menu Access |
This group provides un-restricted access to all menus. This is useful if you want to setup a simple security scheme purely based on restricting access to processes (i.e. forms and browses). Assigning users to this group removes any consideration of menu access. Note: The menu system automatically removes buttons from menus that link to processes for which the user has no access. |
Read-Only Database Access |
This group provides read-only access to all databases but does not allow any changes. This is useful to allow users to look but not touch. |
